The United State of Surveillance: True Holistic Is Here
February 10th, 2020

For a modern trade and market surveillance compliance program to be considered “fully complete,” many would contend that this would translate to leaving no stone unturned when it comes to coverage and functionality. Whether it be as tangible as market data, as exciting as waves in an initial public offering, or something less obvious but potentially more nefarious such as a series of minor security breaches or interoffice text messages, all trade and communications information influencing trade decisions must be assessed and understood as one clear connected narrative.
Enter “holistic surveillance”—the term has been around for almost five years, but as an approach it has undergone a transformation. “Holistic” today is simply not the same thing as the industry described a few years ago. This transformation picked up momentum recently due to significant technology improvements and enhancements.
Today, most financial institutions, regardless of firm type (e.g., buy-side, sell-side) fall somewhere on the spectrum between the “siloed” and “integrated” category when it comes to their holistic surveillance maturity levels (Figure 1). The shift from left to right can depend on the maturity of a financial institution and the compliance functionality required versus what is optimal. That said, some firms are “random” in nature—these firms are typically much smaller and may have yet to establish themselves in a meaningful way. On the other hand, some firms have already begun to use full integrated holistic surveillance, and, as you might expect, these firms typically reflect institutions that are much more developed in their compliance practices.
Figure 1: Best Practice Holistic Surveillance Maturity Model
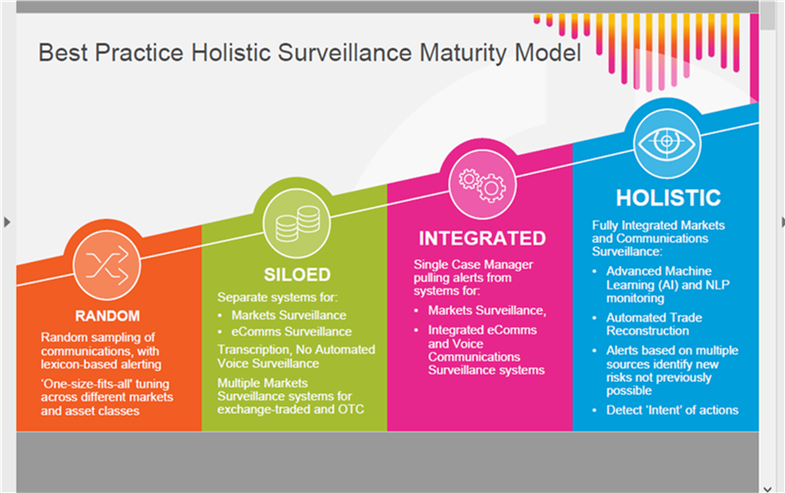
Source: NICE Actimize
With regard to providing a more complete view, holistic surveillance is based on the premise of sourcing all available data inputs, but it also takes the next step forward in contextualizing this data. Compliance professionals can learn how to not only be reactive in nature but to also integrate technology that assists them with preventing malicious instances from occurring.
Communication and trade data often live in isolation, making a seamless comprehensive view of an organization quite the challenge. On top of gathering data from disparate sources, we now have the challenge of understanding relatively new data types. Gone are the days of simple call and put; we are in the age of electronic trading, hashtags, vanishing messages, and systems designed to leave no cyber crumbs behind. To further complicate matters, assuming that data is then collected, we have the task of eliminating the “noise” and identifying relevant context and overlap of unique data elements.
As next-generation advancements—such as machine learning, artificial intelligence, behavioral analytics, smart classifications, and natural language processing—become prominent inclusions within product offerings, users have a greater set of tools to understand intent and decisions made. Going forward, the technology can further progress and become an asset to firms that want to better inform stakeholders about the areas that matter most to them. In this regard, holistic surveillance can also help to “future-proof” organizations from financial or reputational harm. There are fewer instances of manual intervention and greater reliance on sophisticated methods to base investigations and form conclusions.
The following is described in another blog post addressing this subject:
“Holistic surveillance – correlating and analyzing related trade and communications data – is essential to meet regulatory requirements to detect intent and reconstruct trades. It also cuts the time analysts spend chasing false positives by providing them with the context they need to quickly determine if an alert is a false positive or a true violation.”
– Source: Compromise Is Good for Politics, Not Surveillance, February 2019.
Every day, progress is being made to further transform holistic surveillance programs and break down barriers between unique systems in a more logical and meaningful way. On the other hand, communications such as face-to-face conversations, those containing emojis, and most types of social media remain pieces of the puzzle that are difficult to capture. There is also further work to be done around improving our understanding of “intent” and the detection models that prove potential market manipulation or collusion based on the interactions or assessments that are made. For instance, is a smiley face emoji simply a smiley face emoji, or is there malicious intent behind that “smile”?
Despite a few skeptics, the nirvana of true holistic surveillance is here and is ready to adapt—though it just might require firms to take a bold new approach within their compliance programs to get it right. Fully integrated surveillance models can meet many of the toughest regulatory requirements for capturing all types of communications, intent has become decipherable, and automated trade reconstruction is a reality. While the adoption of artificial intelligence is still making strides, the year ahead will take holistic surveillance to a whole new level—and the compliance teams that take proactive steps along the journey will arguably be in the best position to protect their firms in the future.




